Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Google Podcasts | Spotify | TuneIn | RSS
This week, we talk about OWASP and their list of top 10 application security risks. What they are, infamous examples, and what you can do about it.
Download the episode on iTunes or Stitcher and make sure to send us your feedback.
Thanks for listening!
Show Notes
Overview
- OWASP.org
- Top 10 culled from 100s organizations, 1000s applications, 50000 vulnerabilities
- OWASP Store
- OWASP Books
- Troy Hunt – Introducing OWASP top 10 for ASP.NET
- Troy Hunt – OWASP top 10 for ASP.NET on pluralsight
- STRIDE Threats
- Quantify risk with DREAD
#10 Unvalidated Redirects and Forwards
- Don’t do this: http://yoursite.com/redirect.to?http://dont-do-this.com
- Adobe Hack
- See if you were affected via LastPass
#9 Using Components with Known Vulnerabilities
- Vulnerabilities in older versions of Spring Framework
- File Format Vulnerabilities
- List of WordPress Vulnerabilities
#8 Cross-Site Request Forgery (CSRF)
#7 Missing Function Level Access Control
#6 Sensitive Data Exposure
- Plain text data, logging
- Anonymous/Lulsec attacks – Sony / Adobe
- Multi-Hash Password hints
#5 Security Misconfiguration
- Change Default Passwords!
- Verbose Error Pages
- Make sure your up to date!
#4 Insecure Direct Object References
#3 Cross-site Scripting (XSS)
- Stored XSS Attack
- MySpace vs. XSS Worm
- Most prevalent flaw!
#2 Session Management
- Not changing on login
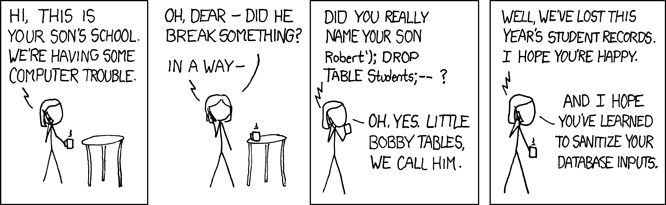
#1 Injection
- SQL – Parameterized, Stored Procs, ORM
- Other Types of Injection, XML, Log
- Sony Attacks
- Sql Injection Hall of Shame
- Bobby Tables
Predictions about the future!
- Joe: Security Misconfiguration moving to top 3
- Allen: XSS on phones!
- Michael: Sensitive data exposure
- Searches in a Post Prism World
Resources
- Security Now! Podcast
- Havij – Advanced Sql Injection
- Metasploit
- Burp Suite
- Fiddler
- OWASP WebGoat
- Gray Hat Python: Python Programming for Hackers and Reverse Engineers
- Audiobooks
Tips / Tricks
- cloudcracker.com
- Ctrl F10 – Run to Cursor, Drag the cursor around
- Mailinator